Securing Your Business: Embracing Cybersecurity as a Service in the Digital Age
Cybersecurity as a Service: Protecting Your Business in the Digital Age
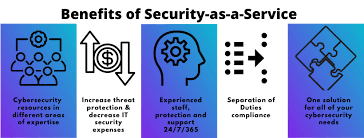
In today’s interconnected world, where businesses heavily rely on technology and digital infrastructure, the need for robust cybersecurity measures has become paramount. Cyber threats are constantly evolving, becoming more sophisticated and challenging to detect. As a result, businesses of all sizes are increasingly turning to cybersecurity as a service (CaaS) to safeguard their sensitive data and protect their operations from potential cyber attacks.
Cybersecurity as a service refers to the outsourcing of cybersecurity functions to specialized providers who offer comprehensive protection against various online threats. These service providers employ cutting-edge technologies, expert knowledge, and industry best practices to deliver proactive security solutions tailored to the specific needs of each business.
One of the key advantages of CaaS is its ability to provide continuous monitoring and threat detection. Cybersecurity experts employ advanced tools and techniques to monitor network traffic, identify anomalies, and detect potential security breaches in real-time. This proactive approach allows for immediate responses and mitigates risks before they can cause significant damage.
Another benefit of CaaS is the access to highly skilled professionals who possess deep expertise in cybersecurity. Small or medium-sized businesses often lack the resources or budget necessary to build an in-house cybersecurity team. By leveraging CaaS, these businesses can tap into a pool of experienced professionals who stay up-to-date with the latest threats, trends, and security protocols. This ensures that businesses receive top-notch protection without having to invest heavily in hiring and training an internal team.
Additionally, CaaS offers scalability and flexibility tailored to each business’s unique requirements. As organizations grow or experience changes in their IT infrastructure, CaaS providers can adapt their services accordingly. This agility allows businesses to focus on their core competencies while leaving the complexities of cybersecurity management in capable hands.
Cost-effectiveness is another significant advantage of opting for CaaS. Traditional cybersecurity approaches often involve substantial upfront investments in hardware, software licenses, and ongoing maintenance costs. With CaaS, businesses can eliminate or significantly reduce these expenses, as they only pay for the services they require. This makes cybersecurity more accessible and affordable, particularly for small and medium-sized enterprises.
Choosing the right CaaS provider is crucial to ensure optimal protection for your business. When selecting a provider, it is essential to consider their expertise, track record, and the range of services they offer. Look for providers who offer comprehensive solutions encompassing vulnerability assessments, threat intelligence, incident response, and ongoing monitoring.
In conclusion, cybersecurity as a service offers businesses a proactive and cost-effective approach to safeguarding their digital assets. By outsourcing cybersecurity functions to specialized providers, businesses can benefit from continuous monitoring, expert knowledge, scalability, and flexibility without incurring excessive costs. In an era where cyber threats are ever-present and evolving rapidly, investing in CaaS is an essential step towards protecting your business in the digital age.
7 Essential Tips for Cybersecurity as a Service in the UK
- Research the company
- Consider your needs
- Check for certifications
- Ask questions
- Test before committing
- Review contracts carefully
- Monitor regularly
Research the company
When it comes to cybersecurity as a service (CaaS), one crucial tip that cannot be emphasized enough is to thoroughly research the company you are considering. Entrusting your business’s cybersecurity to an external provider requires careful evaluation and due diligence.
In today’s digital landscape, where cyber threats are prevalent, it is essential to choose a reputable and reliable CaaS provider. Here are a few key reasons why researching the company is vital:
- Expertise and Experience: Look for a CaaS provider with a proven track record in the cybersecurity industry. Assess their experience, qualifications, and certifications. A reputable provider should have a team of skilled professionals who possess in-depth knowledge of the latest threats and industry best practices.
- Reputation and Reviews: Check for reviews, testimonials, and references from other clients who have used their services. This feedback can provide valuable insights into the quality of their offerings, customer satisfaction levels, and overall performance.
- Compliance and Certifications: Depending on your industry or geographical location, certain compliance standards may apply to your business’s cybersecurity measures. Ensure that the CaaS provider adheres to relevant regulations such as GDPR (General Data Protection Regulation) or ISO 27001 certification.
- Service Offerings: Evaluate whether the CaaS provider offers a comprehensive range of services that align with your business’s specific needs. Consider factors such as threat detection capabilities, incident response protocols, vulnerability assessments, ongoing monitoring, and any additional features they provide.
- Security Measures: Assess the security measures implemented by the CaaS provider to protect their own infrastructure. Inquire about their data encryption practices, access controls, employee background checks, and physical security measures at their facilities.
- Transparency and Communication: A trustworthy CaaS provider should be transparent about their processes, methodologies, and how they handle potential security incidents. Clear communication channels should be established so that you can easily reach out to them in case of any concerns or questions.
- Service Level Agreements (SLAs): Review the SLAs provided by the CaaS provider to understand their commitments regarding response times, uptime guarantees, and incident resolution procedures. Ensure that their SLAs align with your business’s requirements and expectations.
By conducting thorough research on potential CaaS providers, you can make an informed decision that aligns with your business’s cybersecurity needs. Remember, cybersecurity is a critical aspect of protecting your valuable data and ensuring the continuity of your operations. Choosing the right CaaS provider can significantly enhance your overall security posture and provide peace of mind in an increasingly digital world.
Consider your needs
Consider Your Needs: The Key to Choosing the Right Cybersecurity as a Service Provider
When it comes to cybersecurity as a service (CaaS), one size does not fit all. Each business has unique requirements and faces specific cybersecurity challenges. Therefore, it is crucial to consider your needs carefully before choosing a CaaS provider.
Understanding your business’s vulnerabilities and potential risks is the first step. Assess your current IT infrastructure, data sensitivity, and regulatory compliance requirements. Determine the level of protection you need based on the nature of your business and the industry you operate in. This self-evaluation will help you identify the specific cybersecurity services that are essential for your organization.
Once you have a clear understanding of your needs, it’s time to evaluate potential CaaS providers. Look for providers who offer services that align closely with your requirements. Consider their expertise in areas such as network security, data protection, threat intelligence, incident response, and compliance.
Consider the scalability and flexibility offered by each provider. As your business grows or undergoes changes in its IT environment, you will want a CaaS provider who can adapt their services accordingly. Ensure that they can accommodate future expansion or modifications without compromising on security.
Another important factor to consider is the reputation and track record of the CaaS provider. Look for testimonials or case studies from existing clients to gauge their level of customer satisfaction. Check if they have experience working with businesses similar to yours or within your industry.
Cost is always a consideration for any business decision, but it should not be the sole determining factor when choosing a CaaS provider. While budgetary constraints are important, compromising on quality for cost savings can leave your business vulnerable to cyber threats. Focus on finding a balance between affordability and comprehensive protection.
Lastly, communication and collaboration are vital aspects of any successful partnership with a CaaS provider. Ensure that there is open communication channels between both parties so that you can discuss any concerns or questions promptly. A reliable provider will be responsive and proactive in addressing your needs and providing timely support.
By carefully considering your needs, evaluating providers based on their expertise, scalability, reputation, and fostering effective communication, you can choose the right CaaS provider to protect your business from cyber threats effectively. Remember, cybersecurity is not a one-time investment but an ongoing process. Partnering with the right CaaS provider will provide you with peace of mind knowing that your digital assets are in safe hands.
Check for certifications
When considering cybersecurity as a service (CaaS) providers, one essential tip to keep in mind is to check for certifications. In the ever-evolving landscape of cyber threats, it is crucial to partner with a provider that demonstrates a commitment to industry best practices and standards.
Certifications act as proof that a CaaS provider adheres to rigorous security protocols and possesses the necessary expertise to protect your business. Look for certifications such as ISO 27001, which focuses on information security management systems, or SOC 2 Type II, which verifies that the provider has effective controls in place for security, availability, processing integrity, confidentiality, and privacy.
These certifications indicate that the CaaS provider has undergone comprehensive audits by independent third-party organizations. They validate that the provider has implemented robust security measures and follows established guidelines in safeguarding data and managing potential risks.
By partnering with a certified CaaS provider, you can have confidence in their ability to protect your sensitive information and mitigate potential cyber threats effectively. Certifications demonstrate their commitment to maintaining high standards of security and continuously improving their practices.
It’s important not to solely rely on claims made by CaaS providers regarding their security measures. Verifying certifications helps you make an informed decision based on objective evidence of their capabilities.
In summary, when selecting a CaaS provider, checking for certifications is an essential tip to ensure you are partnering with a trusted and reliable organization. By doing so, you can have peace of mind knowing that your business’s cybersecurity needs are being handled by experts who adhere to industry-recognized standards and best practices.
Ask questions
When it comes to ensuring the security of your business in the digital age, cybersecurity as a service (CaaS) has become an increasingly popular choice. As you explore different CaaS providers and evaluate their offerings, one crucial tip stands out: ask questions.
Asking questions is an essential step in understanding the capabilities and suitability of a CaaS provider for your specific business needs. Here are a few key inquiries to consider:
- What services do they provide? It’s important to have a clear understanding of the range of services offered by the CaaS provider. Do they offer comprehensive solutions that cover vulnerability assessments, threat intelligence, incident response, and ongoing monitoring? Make sure their services align with your business requirements.
- How experienced is their team? Inquire about the expertise and qualifications of the cybersecurity professionals who will be responsible for protecting your business. Ask about their certifications, industry experience, and ongoing training to ensure they stay up-to-date with emerging threats and best practices.
- What is their approach to threat detection and response? Understanding how the provider detects and responds to potential threats is crucial. Ask about their monitoring capabilities, tools used for threat detection, and response protocols in case of an incident. A proactive approach that includes real-time monitoring is highly desirable.
- Can they accommodate your business’s unique needs? Every business has its own set of requirements and challenges when it comes to cybersecurity. Make sure the CaaS provider can tailor their services to meet your specific needs. Whether it’s compliance regulations, industry-specific vulnerabilities, or unique IT infrastructure considerations, ensure they can address these aspects effectively.
- How do they handle data privacy and compliance? Data privacy regulations such as GDPR require businesses to handle customer data responsibly. Inquire about the measures taken by the CaaS provider to protect data privacy and ensure compliance with relevant regulations.
- What is their track record? Request information on past successes or case studies that demonstrate the provider’s ability to protect businesses against cyber threats. This will give you an idea of their experience and effectiveness in safeguarding sensitive information.
By asking these questions, you can gain valuable insights into a CaaS provider’s capabilities, expertise, and suitability for your business. Remember, cybersecurity is a critical aspect of your operations, and choosing the right partner is essential in maintaining the integrity and security of your digital assets.
So, don’t hesitate to ask questions. It’s your business’s security on the line, and thorough inquiries will help you make an informed decision when selecting a CaaS provider that best fits your needs.
Test before committing
When it comes to cybersecurity as a service (CaaS), one valuable tip that businesses should always keep in mind is to test before committing. Before finalizing an agreement with a CaaS provider, it is crucial to thoroughly evaluate their services and ensure they meet your specific requirements.
Testing allows you to assess the effectiveness and reliability of the CaaS provider’s cybersecurity solutions before making a long-term commitment. It provides an opportunity to gauge their capabilities in detecting and mitigating potential threats, as well as their response time in case of an incident.
During the testing phase, consider conducting vulnerability assessments or penetration tests to identify any weaknesses in your system’s security. This process will help you understand how well the CaaS provider can protect your business against real-world cyber threats.
Moreover, testing allows you to evaluate the compatibility and integration of the CaaS solution with your existing IT infrastructure. Ensure that the service seamlessly integrates with your systems without causing disruptions or compatibility issues.
Additionally, take this opportunity to assess the level of support provided by the CaaS provider. Prompt and reliable support is vital in times of crisis or when urgent assistance is required. Testing their responsiveness and availability will give you confidence in their ability to handle any cybersecurity incidents effectively.
By testing before committing, you can make an informed decision about whether the CaaS provider aligns with your business needs and objectives. It gives you peace of mind knowing that you have thoroughly evaluated their capabilities and are confident in their ability to protect your digital assets.
Remember, cybersecurity is not a one-size-fits-all solution. Each business has unique requirements and faces specific threats. Testing allows you to tailor the CaaS solution according to your specific needs, ensuring that it provides optimal protection for your organization.
In conclusion, testing before committing is a crucial step when considering cybersecurity as a service. It enables businesses to evaluate the effectiveness, compatibility, and support provided by potential providers. By conducting thorough tests, businesses can make an informed decision and choose a CaaS provider that best meets their cybersecurity needs, ultimately safeguarding their digital assets in today’s ever-evolving threat landscape.
Review contracts carefully
When it comes to cybersecurity as a service (CaaS), one crucial tip that businesses should always keep in mind is to review contracts carefully.
Engaging with a CaaS provider involves entering into a contractual agreement, outlining the terms and conditions of the service. This agreement serves as a legal framework that defines the responsibilities, obligations, and rights of both parties involved.
Reviewing contracts thoroughly before signing is essential to ensure that your business’s cybersecurity needs are adequately addressed and protected. Here are a few key points to consider during contract review:
- Scope of Services: Take the time to understand the specific services offered by the CaaS provider. Ensure that they align with your business requirements and cover all critical aspects of cybersecurity, such as threat detection, incident response, and ongoing monitoring.
- Service Level Agreements (SLAs): Pay close attention to SLAs, which outline performance metrics and guarantees provided by the CaaS provider. Look for details regarding response times, system availability, and incident resolution procedures. Clear SLAs help set expectations and hold the provider accountable for delivering quality services.
- Data Protection: Cybersecurity involves protecting sensitive data from unauthorized access or breaches. Review how the CaaS provider handles data protection measures, including encryption protocols, access controls, and compliance with relevant data protection regulations (such as GDPR).
- Incident Response: Assess how the CaaS provider handles security incidents or breaches. Look for defined procedures outlining their response plan, communication protocols during incidents, and any liability or compensation clauses in case of failures.
- Termination Clause: Understand the termination conditions outlined in the contract. Ensure that you have flexibility in ending the agreement if necessary while also considering any exit costs or data retrieval processes.
- Confidentiality and Non-Disclosure: Cybersecurity requires trust between both parties involved. Verify that confidentiality and non-disclosure clauses are included in the contract to protect your business’s sensitive information from being shared or misused.
- Scalability and Flexibility: Consider your business’s future growth and changing needs. Ensure that the contract allows for scalability and flexibility, allowing you to adjust services as your business evolves.
By carefully reviewing contracts before engaging with a CaaS provider, businesses can mitigate potential risks, ensure adequate protection of their data, and establish a clear understanding of the services provided. This attention to detail helps build a strong foundation for a secure and successful partnership in safeguarding your business against cyber threats.
Monitor regularly
In today’s digital landscape, where cyber threats are constantly evolving, it has become crucial for businesses to prioritize cybersecurity. One effective strategy to ensure the safety of your digital assets is to embrace cybersecurity as a service (CaaS). Within this framework, one important tip stands out: regular monitoring.
Regular monitoring is a fundamental aspect of CaaS that helps detect and prevent potential cyber attacks before they can cause significant damage. By continuously monitoring your network and systems, cybersecurity experts can identify any suspicious activities or anomalies that may indicate a breach or an attempted intrusion.
Through advanced tools and technologies, CaaS providers can actively monitor network traffic, user behavior, and system logs in real-time. This proactive approach allows them to swiftly respond to any potential threats or vulnerabilities. By promptly addressing these issues, they can minimize the impact on your business operations and protect sensitive data from falling into the wrong hands.
Regular monitoring also enables CaaS providers to stay ahead of emerging threats. Cybercriminals are constantly developing new tactics and techniques to bypass security measures. By closely observing network patterns and staying up-to-date with the latest threat intelligence, CaaS experts can adapt their strategies accordingly. This ensures that your business remains protected against the ever-evolving landscape of cyber threats.
Moreover, regular monitoring provides valuable insights into your system’s overall security posture. It allows you to identify any potential weaknesses or vulnerabilities that may exist within your infrastructure. Armed with this knowledge, you can take proactive steps to strengthen your security measures and mitigate risks effectively.
By embracing regular monitoring as part of your cybersecurity strategy through CaaS, you gain peace of mind knowing that a team of dedicated professionals is continuously keeping an eye on your digital environment. Their expertise and vigilance allow them to swiftly respond to any potential threats or incidents.
Remember, cybersecurity is not a one-time investment but an ongoing process that requires constant attention. Regular monitoring is a key component of this process as it helps ensure the safety and integrity of your digital assets. By partnering with a reliable CaaS provider, you can establish a strong line of defense against cyber threats and protect your business from potential harm.