Exploring the Diverse Types of Cybersecurity: Safeguarding Your Digital World
Types of Cybersecurity: Safeguarding Your Digital World
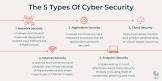
In today’s interconnected world, cybersecurity has become a critical concern for individuals and businesses alike. As our reliance on technology grows, so does the need to protect our digital assets from malicious actors. Cybersecurity encompasses a wide range of measures and techniques designed to safeguard computer systems, networks, and data from unauthorized access, theft, or damage. Let’s explore some of the key types of cybersecurity that play a vital role in keeping our digital world secure.
Network Security:
Network security focuses on protecting computer networks from unauthorized access or misuse. It involves implementing firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), and other mechanisms to prevent unauthorized individuals from gaining access to sensitive information or disrupting network operations.
Application Security:
Application security involves securing software applications and programs against potential vulnerabilities that could be exploited by hackers. This includes conducting regular code reviews, using encryption techniques for data transmission, and implementing secure coding practices during the development process.
Cloud Security:
With the growing popularity of cloud computing services, cloud security has become increasingly important. It focuses on protecting data stored in cloud platforms by employing strong authentication measures, encryption techniques, and robust access controls. Additionally, regular audits and monitoring help ensure compliance with industry standards.
Data Loss Prevention (DLP):
Data is one of the most valuable assets for any organization. Data loss prevention aims to prevent unauthorized users from accessing or exfiltrating sensitive information. This is achieved through various methods such as encryption, access controls, user training programs, and implementing data backup strategies to mitigate the risk of permanent data loss.
Endpoint Security:
Endpoint devices such as laptops, smartphones, and tablets are often vulnerable entry points for cyber threats. Endpoint security involves securing these devices through measures such as antivirus software installation, regular patching and updating of operating systems and applications, as well as implementing device encryption and remote wipe capabilities.
Social Engineering Prevention:
Social engineering refers to the manipulation of individuals to gain unauthorized access or extract sensitive information. Cybersecurity measures against social engineering include user awareness training, implementing strong password policies, multi-factor authentication, and email filtering to detect and block phishing attempts.
Incident Response:
No cybersecurity strategy is complete without a robust incident response plan. This involves having predefined procedures in place to detect, respond to, and recover from security incidents effectively. Incident response plans typically include steps for containment, investigation, eradication of threats, as well as post-incident analysis to prevent future occurrences.
Mobile Device Security:
As mobile devices become ubiquitous in both personal and professional settings, securing them against cyber threats is crucial. Mobile device security encompasses measures such as device encryption, remote tracking and wiping capabilities, app permission management, and secure app development practices.
In conclusion, cybersecurity is a multifaceted discipline that requires a comprehensive approach to protect our digital world from evolving threats. By implementing various types of cybersecurity measures like network security, application security, cloud security, data loss prevention (DLP), endpoint security, social engineering prevention, incident response planning, and mobile device security; individuals and organizations can significantly reduce their risk exposure and safeguard their valuable digital assets.
9 Essential Tips for Effective Cyber Security: Safeguard Your Digital World
- Use strong passwords and change them regularly.
- Install anti-virus software and keep it up to date.
- Be careful about what you share online, including personal information and financial details.
- Back up your data regularly in case of a cyber attack or other system failure.
- Secure your Wi-Fi network with a strong password and encryption protocols such as WPA2 or WPA3.
- Use two-factor authentication when available to add an extra layer of security to your accounts and devices.
- Be aware of phishing emails, which can be used by hackers to gain access to your accounts or systems by pretending to be from legitimate companies or people that you trust
- Be mindful of what websites you visit, as some may contain malicious code designed to steal information from your device
- Keep all software updated with the latest security patches
Use strong passwords and change them regularly.
Use Strong Passwords and Change Them Regularly: A Crucial Cybersecurity Tip
In an era where our lives are increasingly intertwined with technology, protecting our digital presence has become more important than ever. One fundamental cybersecurity practice that cannot be overstated is the use of strong passwords and regular password changes. By following this simple yet effective tip, you can significantly enhance your online security.
A strong password acts as a robust barrier against unauthorized access to your accounts and sensitive information. It is essential to create passwords that are unique, complex, and difficult for others to guess. Here are some key considerations when crafting a strong password:
Length: Opt for passwords that are at least 12 characters long. The longer the password, the harder it is for hackers to crack.
Complexity: Include a combination of uppercase and lowercase letters, numbers, and special characters in your password. Avoid using easily guessable patterns or common phrases.
Avoid Personal Information: Steer clear of using personal information such as your name, birthdate, or address in your passwords. Hackers often exploit such details to gain unauthorized access.
Unique for Each Account: It’s crucial to use different passwords for each online account you have. Reusing passwords across multiple accounts increases the risk of multiple accounts being compromised if one password is breached.
In addition to creating strong passwords, it is equally important to change them regularly. Regular password changes help mitigate the potential impact of any security breaches or unauthorized access attempts. Aim to change your passwords every three to six months or sooner if you suspect any suspicious activity on your accounts.
Remembering multiple complex passwords can be challenging, but there are strategies to help manage them effectively:
Password Managers: Consider using a reputable password manager tool that securely stores all your passwords in an encrypted vault accessible through a master password or biometric authentication.
Two-Factor Authentication (2FA): Enable two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a unique code sent to your mobile device, in addition to your password.
By implementing the practice of using strong passwords and changing them regularly, you significantly reduce the risk of falling victim to cyber attacks. Take control of your online security today and protect your valuable digital assets from malicious actors.
Install anti-virus software and keep it up to date.
Install Anti-Virus Software and Keep It Up to Date: A Crucial Step in Cybersecurity
In the ever-evolving landscape of cyber threats, protecting your digital devices from malicious software is of paramount importance. One of the most effective ways to defend against viruses, malware, and other cyber-attacks is by installing reliable anti-virus software and ensuring it remains up to date.
Anti-virus software acts as a shield for your computer, identifying and eliminating potential threats that could compromise your data or disrupt your system. It scans files, programs, and attachments for known patterns or behaviors associated with malicious code, providing you with an added layer of security.
Regularly updating your anti-virus software is vital. Cybercriminals are continually developing new techniques to exploit vulnerabilities in operating systems and applications. By keeping your anti-virus software up to date, you ensure that it has the latest virus definitions and security patches needed to detect and neutralize emerging threats.
Installing anti-virus software is a straightforward process. Many reputable companies offer both free and paid versions of their products. Choose one that suits your needs and budget, ensuring it provides real-time scanning capabilities along with regular updates.
Once installed, configure the software to perform automatic scans on a regular basis. This proactive approach helps identify any potential threats before they can cause harm. Additionally, schedule regular system scans to thoroughly examine all files stored on your computer for any hidden malware that may have slipped past initial detection.
While anti-virus software is a powerful tool in cybersecurity, it should not be relied upon as the sole means of protection. It is essential to practice safe online habits such as avoiding suspicious websites or links, being cautious when opening email attachments from unknown sources, and regularly backing up important data.
Remember that cyber threats are constantly evolving; therefore, it’s crucial to keep both your operating system and applications up to date with the latest security patches. Regularly check for updates from software vendors and install them promptly to mitigate potential vulnerabilities that cybercriminals may exploit.
By installing anti-virus software and keeping it up to date, you take a significant step towards safeguarding your digital world. This simple yet crucial measure provides you with peace of mind, knowing that your computer is protected against the ever-present threat of viruses and malware. Stay vigilant, stay updated, and stay secure in the digital realm.
Be careful about what you share online, including personal information and financial details.
Be Mindful of Your Online Sharing: Protecting Personal and Financial Information
In today’s digital age, where virtually every aspect of our lives is intertwined with the internet, it’s crucial to be cautious about what we share online. With cyber threats on the rise, protecting our personal information and financial details has become paramount. Let’s delve into why being careful about online sharing is an essential tip for safeguarding your digital security.
When it comes to personal information, it’s important to remember that once something is shared online, it can potentially stay there forever. Be mindful of the information you disclose on social media platforms, such as your full name, address, phone number, or even birthdate. Cybercriminals can exploit this information for identity theft or other malicious activities.
Financial details are particularly sensitive and require extra caution. Avoid sharing credit card numbers, bank account details, or any other confidential financial information in public forums or unsecured websites. Always ensure that you are using secure and encrypted connections when conducting online transactions.
To protect yourself further:
- Regularly review your privacy settings on social media platforms and adjust them according to your comfort level. Limit the visibility of your personal information to trusted individuals.
- Be cautious about accepting friend requests or connections from unknown individuals. Verify their identities before sharing any personal or financial details.
- Use strong and unique passwords for all your online accounts and enable two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification.
- Be wary of phishing attempts through emails, messages, or phone calls asking for personal or financial information. Legitimate organizations will never ask you to provide sensitive data through these channels.
- Keep your devices up to date with the latest security patches and antivirus software to protect against malware and other cyber threats.
Remember that protecting your personal and financial information is a shared responsibility between individuals and service providers alike. By being mindful of what you share online and following these best practices, you can significantly reduce the risk of falling victim to cybercrime and maintain your digital security. Stay vigilant, stay safe!
Back up your data regularly in case of a cyber attack or other system failure.
Back Up Your Data Regularly: A Crucial Step in Cybersecurity
In today’s digital landscape, where cyber threats loom large and system failures can occur unexpectedly, backing up your data regularly is a fundamental step in ensuring the safety and integrity of your valuable information. Whether it’s personal files, business documents, or sensitive customer data, losing important data can be devastating. Therefore, implementing a robust backup strategy is essential to mitigate the risks associated with cyber attacks or system failures.
Cyber attacks can take various forms, such as ransomware, malware infections, or unauthorized access by hackers. These threats can result in data loss or encryption that renders your files inaccessible unless a ransom is paid. By regularly backing up your data to an external storage device or cloud-based service, you create an additional layer of protection against such incidents.
Similarly, system failures like hardware malfunctions or software errors can lead to data corruption or loss. Without a recent backup, recovering this lost data becomes incredibly challenging and sometimes impossible. By adhering to a regular backup routine, you ensure that even if a system failure occurs, you have a recent copy of your files that can be easily restored.
When implementing a backup strategy for cybersecurity purposes:
- Determine what needs to be backed up: Identify critical files and databases that must be included in your backup process. This could include financial records, customer information, project files, or any other data that is vital for your operations.
- Choose the right backup method: Consider using both local and remote backups for added security. Local backups involve storing copies of your data on external hard drives or network-attached storage (NAS) devices within your premises. Remote backups utilize cloud-based services that securely store your data on remote servers accessible through the internet.
- Set up automated backups: Manually performing backups increases the risk of forgetting or neglecting this crucial task. Instead, schedule automated backups at regular intervals to ensure that your data is consistently and reliably protected. This can be done using backup software or built-in backup features provided by operating systems.
- Test your backups: Regularly verify the integrity of your backups by performing test restores. This ensures that the backed-up data is accessible and can be successfully restored when needed. Testing also helps identify any potential issues with the backup process, allowing you to address them promptly.
- Store backups securely: Treat your backup copies with the same level of security as your original data. If using physical storage devices, keep them in a secure location away from potential hazards like fire or theft. For cloud-based backups, choose reputable service providers that offer robust security measures and encryption.
By following these steps and making regular data backups a priority, you significantly enhance your ability to recover from cyber attacks or system failures swiftly and minimize disruption to your personal or business operations. Remember, data loss can happen unexpectedly, but with a reliable backup strategy in place, you gain peace of mind knowing that your valuable information is safeguarded against unforeseen circumstances.
Secure your Wi-Fi network with a strong password and encryption protocols such as WPA2 or WPA3.
Secure Your Wi-Fi Network: Protecting Your Digital Gateway
In today’s interconnected world, Wi-Fi networks have become the backbone of our digital lives. From streaming entertainment to conducting business transactions, we rely heavily on the convenience and accessibility that Wi-Fi provides. However, it is essential to remember that an unsecured Wi-Fi network can leave you vulnerable to cyber threats. One crucial step in safeguarding your Wi-Fi network is ensuring it is protected with a strong password and encryption protocols such as WPA2 or WPA3.
A strong password acts as the first line of defense against unauthorized access to your Wi-Fi network. Avoid using easily guessable passwords like “123456” or “password.” Instead, create a unique and complex password that includes a combination of uppercase and lowercase letters, numbers, and special characters. The longer and more intricate your password is, the harder it becomes for hackers to crack.
Encryption protocols play a vital role in securing your wireless network by scrambling the data transmitted between devices connected to it. WPA2 (Wi-Fi Protected Access 2) has been widely used for years and offers solid protection against most common attacks. However, with advancing technology comes stronger security measures. WPA3 is the latest standard that provides enhanced encryption algorithms and better safeguards against potential vulnerabilities.
To secure your Wi-Fi network with WPA2 or WPA3 encryption protocols, access your router’s settings through its web interface. Look for the wireless security settings section, where you can select either WPA2 or WPA3 as the encryption method. Remember to save the changes once you’ve made your selection.
By securing your Wi-Fi network with a strong password and encryption protocols such as WPA2 or WPA3, you significantly reduce the risk of unauthorized access and potential data breaches. It acts as a digital gateway protector, ensuring only authorized users can connect to your network while keeping sensitive information safe from prying eyes.
Remember, cybersecurity is an ongoing effort. Regularly update your Wi-Fi router’s firmware to benefit from the latest security patches and enhancements. Additionally, consider changing your Wi-Fi password periodically to maintain a robust defense against potential threats.
By implementing these simple yet effective measures, you can enjoy the convenience of a wireless network while keeping your digital world secure. So, take a moment to secure your Wi-Fi network today and enjoy peace of mind knowing that you are taking proactive steps to protect yourself and your digital assets.
Use two-factor authentication when available to add an extra layer of security to your accounts and devices.
Enhance Your Cybersecurity with Two-Factor Authentication
In an increasingly digital world, protecting our online accounts and devices from unauthorized access has become more crucial than ever. One effective way to bolster your cybersecurity is by utilizing two-factor authentication (2FA), an additional layer of security that provides an extra barrier against potential threats. Let’s explore why implementing 2FA is a smart move and how it can safeguard your valuable information.
Two-factor authentication adds an extra step to the login process, requiring users to provide two forms of identification before accessing their accounts or devices. Typically, this involves combining something you know (such as a password) with something you have (such as a unique code or physical device). This combination significantly reduces the risk of unauthorized access, even if someone manages to obtain your password.
One common form of 2FA is receiving a verification code via SMS or email after entering your password. This code is usually time-sensitive and must be entered correctly to gain access. Another popular method involves using authenticator apps, such as Google Authenticator or Microsoft Authenticator, which generate unique codes on your smartphone that change periodically.
By implementing 2FA, you create an additional barrier that cybercriminals must overcome in order to breach your accounts or devices. Even if they manage to steal or guess your password, they would still need the second factor (e.g., the verification code) to gain entry. This significantly reduces the likelihood of successful attacks and provides peace of mind knowing that your sensitive information remains secure.
Furthermore, 2FA is widely supported by various online platforms and services, including social media accounts, email providers, banking institutions, and cloud storage platforms. Take advantage of this feature whenever it’s available and ensure that you enable it for all relevant accounts. Many platforms provide clear instructions on how to set up 2FA within their security settings.
While two-factor authentication offers enhanced security, it’s important to remember that it’s not foolproof. It’s still crucial to maintain good password hygiene by using strong, unique passwords for each of your accounts and regularly updating them. Additionally, stay vigilant against phishing attempts or suspicious activities, as no security measure can completely eliminate all risks.
In conclusion, two-factor authentication is a valuable tool in the fight against cyber threats. By implementing this additional layer of security, you significantly reduce the risk of unauthorized access to your accounts and devices. Take advantage of 2FA whenever it’s available and enjoy the peace of mind that comes with knowing your digital world is better protected.
Be aware of phishing emails, which can be used by hackers to gain access to your accounts or systems by pretending to be from legitimate companies or people that you trust
Protect Yourself from Phishing Emails: Stay One Step Ahead of Hackers
In today’s digital landscape, where communication happens primarily through email, it is crucial to be aware of the potential dangers lurking in your inbox. Phishing emails have become a common tactic used by hackers to gain unauthorized access to your accounts or systems. These deceptive emails disguise themselves as legitimate messages from trusted companies or individuals, tricking unsuspecting victims into sharing sensitive information or clicking on malicious links. To safeguard yourself and your digital assets, it is essential to stay vigilant and recognise the signs of phishing emails.
Phishing emails often employ various techniques to appear genuine and trustworthy. They may mimic the logos, email addresses, and writing styles of well-known organizations or individuals you regularly interact with. Here are some tips to help you identify and protect yourself from phishing attempts:
- Scrutinize the sender’s email address: Pay close attention to the sender’s email address. Hackers may use addresses that look similar but contain slight variations or misspellings of legitimate ones. Always double-check before responding or clicking on any links.
- Examine the content carefully: Phishing emails often create a sense of urgency or fear to prompt immediate action. Be cautious if an email demands urgent personal information, financial details, or login credentials. Legitimate companies usually do not request such sensitive information via email.
- Beware of suspicious attachments or links: Be cautious when opening attachments or clicking on links in emails, especially if they come from unknown sources or seem out of context. Hover over links (without clicking) to check their destination URLs; if they appear suspicious, refrain from interacting with them.
- Check for grammatical errors and inconsistencies: Phishing emails often contain grammatical errors, typos, or inconsistent formatting that can give them away as fraudulent attempts. Legitimate organizations typically maintain a high standard for their communications.
- Verify requests independently: If an email asks you to take action, such as providing personal information or making a payment, independently verify the request through official channels. Contact the company or individual directly using their official contact information, rather than relying on the details provided in the suspicious email.
- Keep your software up to date: Regularly update your operating system, web browsers, and security software to ensure you have the latest protection against known vulnerabilities and phishing attempts.
By being aware of phishing emails and implementing these precautions, you can significantly reduce the risk of falling victim to cybercriminals. Remember, it is always better to err on the side of caution when it comes to sharing sensitive information online. Stay vigilant, trust your instincts, and protect yourself from phishing attempts that aim to compromise your accounts or systems.
Be mindful of what websites you visit, as some may contain malicious code designed to steal information from your device
Staying Vigilant: Protecting Yourself Online
In today’s digital landscape, being mindful of the websites we visit is crucial to safeguard our personal information and devices. Cybercriminals often exploit unsuspecting users by embedding malicious code in websites, aiming to steal sensitive data or gain unauthorized access to devices. By following a few simple practices, we can significantly reduce the risk of falling victim to such attacks.
Firstly, it is essential to be cautious when clicking on links or visiting unfamiliar websites. Stick to reputable sources and avoid clicking on suspicious links received through emails or messages from unknown senders. These links may redirect you to fraudulent websites designed to deceive and compromise your device’s security.
Secondly, keep your web browser and antivirus software up to date. Regularly updating these tools ensures that you have the latest security patches and protection against known vulnerabilities. Additionally, enable automatic updates whenever possible for seamless protection against emerging threats.
Furthermore, consider using a reliable ad-blocker or script-blocking extension for your web browser. These tools help prevent potentially harmful scripts from running on websites you visit, reducing the risk of encountering malicious code.
Another valuable practice is to look for HTTPS (Hypertext Transfer Protocol Secure) in the website’s URL before entering any sensitive information. Websites that use HTTPS encrypt data transmitted between your device and their servers, making it harder for cybercriminals to intercept and steal your data.
In addition, consider using a virtual private network (VPN) when browsing the internet. A VPN encrypts your internet traffic and masks your IP address, providing an extra layer of security and anonymity while accessing websites. This can help protect your data from being intercepted or monitored by malicious actors.
Lastly, trust your instincts and exercise caution when visiting unfamiliar websites or encountering pop-up advertisements. If something seems suspicious or too good to be true, it probably is. Avoid providing personal information unless you are confident in the website’s legitimacy.
By being mindful of the websites we visit and following these simple tips, we can significantly reduce the risk of falling victim to cyber attacks. Remember, staying vigilant and informed is key to protecting yourself online in this ever-evolving digital landscape.
Keep all software updated with the latest security patches
Keeping All Software Updated: A Crucial Step in Cybersecurity
In the ever-evolving landscape of cybersecurity, staying one step ahead of potential threats is essential. One simple yet effective tip to enhance your digital security is to keep all software updated with the latest security patches. Whether it’s your operating system, antivirus software, or applications, regular updates play a vital role in safeguarding your digital world.
Software updates often include crucial security patches that address vulnerabilities identified by developers or reported by users. These vulnerabilities can be exploited by cybercriminals to gain unauthorized access to your systems, steal sensitive data, or cause other forms of harm. By promptly applying these updates, you close potential entry points for attackers and strengthen your defenses.
Operating system updates are particularly important as they provide security enhancements and bug fixes that protect against various types of cyber threats. Outdated operating systems may have known vulnerabilities that hackers can exploit easily. Regularly checking for and installing operating system updates ensures that you benefit from the latest security measures and stay protected.
Antivirus software updates are equally vital in maintaining robust cybersecurity. Antivirus vendors continuously update their software to combat new types of malware and hacking techniques. These updates include virus definition files that help the antivirus program identify and block emerging threats effectively. Failing to update your antivirus software regularly may leave you susceptible to new malware strains that could compromise your data or privacy.
Updating applications is another critical aspect of keeping your digital environment secure. Many cyberattacks target vulnerabilities in specific applications rather than the entire system. Developers frequently release updates that address these vulnerabilities and enhance application security. Neglecting application updates increases the risk of exploitation by cybercriminals who are constantly searching for weaknesses to exploit.
In addition to addressing security concerns, software updates often bring performance improvements and new features that enhance user experience. By keeping your software up-to-date, you not only fortify your defenses but also enjoy a smoother and more efficient computing experience.
To streamline the update process, consider enabling automatic updates whenever possible. This ensures that you receive the latest security patches without having to manually check for updates regularly. However, it’s important to verify that automatic updates are enabled for all software, including the operating system, antivirus software, and applications.
In conclusion, keeping all software updated with the latest security patches is a fundamental step in maintaining robust cybersecurity. By promptly applying updates for your operating system, antivirus software, and applications, you proactively protect yourself against potential vulnerabilities and stay one step ahead of cyber threats. Remember: regular updates not only enhance your security but also improve overall performance. Stay vigilant and make software updates a priority in your digital routine.