iBoss Cloud: Empowering Businesses with Advanced Cloud-Based Security Solutions
iBoss Cloud: The Future of Secure Web Gateway Solutions
In today’s digital age, businesses face an ever-increasing number of cybersecurity threats. Protecting sensitive data, ensuring regulatory compliance, and maintaining a productive work environment are paramount concerns for organizations worldwide. This is where iBoss Cloud comes into play as a leading secure web gateway solution.
What is iBoss Cloud?
iBoss Cloud is a comprehensive cloud-based security platform that offers advanced web filtering, data loss prevention, malware defense, and network protection. It provides organizations with the tools they need to safeguard their networks, users, and data from evolving cyber threats.
Key Features and Benefits
Advanced Web Filtering: iBoss Cloud employs advanced AI-powered web filtering technology to block access to malicious or inappropriate websites. It enables organizations to enforce internet usage policies effectively while ensuring a safe browsing experience for employees.
Data Loss Prevention (DLP): With built-in DLP capabilities, iBoss Cloud allows businesses to identify and prevent the unauthorized transmission of sensitive information. This ensures compliance with industry regulations and protects against data breaches.
Malware Defense: iBoss Cloud utilizes real-time threat intelligence and behavior analytics to detect and block malware in real-time. By analyzing network traffic patterns and identifying suspicious activities, it prevents malicious software from infiltrating systems.
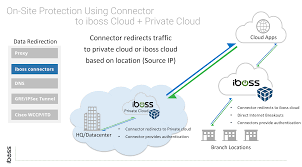
Secure Remote Access: In an era where remote work is increasingly prevalent, iBoss Cloud provides secure remote access solutions. It allows employees to connect securely to corporate networks from any location without compromising network security.
Scalability and Flexibility: As a cloud-based solution, iBoss Cloud offers scalability and flexibility that traditional on-premises solutions cannot match. It can adapt seamlessly to the changing needs of growing organizations without requiring significant hardware investments or infrastructure upgrades.
Simplified Management: iBoss Cloud provides a centralized management console that simplifies administration tasks such as policy creation, user management, and reporting. This intuitive interface allows IT teams to efficiently monitor and control network activity, saving valuable time and resources.
Why Choose iBoss Cloud?
iBoss Cloud stands out among other secure web gateway solutions due to its unique combination of advanced features, cloud-based architecture, and comprehensive threat intelligence. Here are a few reasons why organizations choose iBoss Cloud:
Proactive Threat Detection: iBoss Cloud’s advanced threat intelligence continuously monitors global cyber threats, enabling proactive detection and prevention of emerging threats.
Enhanced Productivity: By filtering out non-work-related websites and applications, iBoss Cloud helps organizations boost employee productivity by minimizing distractions.
Cost-Effectiveness: With no hardware or software installations required, iBoss Cloud eliminates the need for costly upfront investments. It also reduces ongoing maintenance costs associated with traditional on-premises solutions.
Global Coverage: iBoss Cloud operates through a global network of data centers, ensuring fast and reliable connectivity for users worldwide.
Conclusion
In an era where cybersecurity threats continue to evolve rapidly, organizations need robust solutions that can adapt to these challenges effectively. iBoss Cloud offers a comprehensive suite of features that protect networks, users, and data from a wide range of cyber threats. With its cloud-based architecture, scalability, and advanced threat intelligence capabilities, it is paving the way for the future of secure web gateway solutions. Embracing iBoss Cloud can help businesses stay one step ahead in the ongoing battle against cybercrime while maintaining productivity and compliance in today’s digital landscape.
9 Advantages of iBoss Cloud: Simplified Usage and Deployment, Secure Access Anywhere, Advanced Threat Protection, Precise Policy Enforcement, Extensive Visibility & Reporting, Real-Time Monitoring & Alerting, Multi-Tenancy Support, Seamless Integration with
- Easy to use and deploy
- Secure access from anywhere
- Advanced threat protection
- Granular policy enforcement
- Comprehensive visibility & reporting
- Real-time monitoring & alerting
- Multi-tenancy support
- Integration with leading identity providers
- 24/7 customer support
Drawbacks of iboss Cloud: High Cost, Limited Features, Poor Support, Security Concerns
Easy to use and deploy
Easy to Use and Deploy: Embracing the Simplicity of iBoss Cloud
In today’s fast-paced business environment, time is of the essence. Organizations need solutions that can be implemented quickly and seamlessly without adding complexity to their operations. This is where iBoss Cloud shines, offering a remarkable advantage with its easy-to-use and deploy features.
Designed with user-friendliness in mind, iBoss Cloud eliminates the need for hardware installations or software deployments. This means that businesses can get up and running without the hassle of complex setup processes or extensive IT expertise. With just a few simple steps, organizations can start benefiting from the robust security features offered by iBoss Cloud.
The simplicity of iBoss Cloud extends beyond its initial deployment. Once implemented, managing and maintaining the solution becomes a breeze. The intuitive interface provided by iBoss Cloud allows IT administrators to easily navigate through various settings and configurations, enabling them to efficiently manage policies, user access, and reporting.
Not only does this ease of use save valuable time for IT teams, but it also reduces the learning curve for end-users. Employees can quickly adapt to the platform’s straightforward interface, ensuring that they can make the most out of its features without requiring extensive training.
Furthermore, as a cloud-based solution, iBoss Cloud offers unparalleled flexibility. Businesses can scale their operations up or down effortlessly without worrying about hardware limitations or compatibility issues. This flexibility allows organizations to adapt to changing business needs rapidly while keeping costs under control.
By removing the complexities associated with traditional on-premises solutions, iBoss Cloud empowers businesses to focus on what matters most – their core operations. With simplified deployment and management processes, organizations can allocate more time and resources towards driving innovation and achieving their strategic goals.
In conclusion, iBoss Cloud’s ease of use and deployment capabilities set it apart as an exceptional solution for businesses seeking efficient cybersecurity measures. By eliminating the need for hardware or software installations while providing a user-friendly interface, iBoss Cloud enables organizations to quickly implement robust security measures without adding unnecessary complexity. Embrace the simplicity of iBoss Cloud and pave the way for enhanced productivity, streamlined operations, and peace of mind in today’s ever-evolving digital landscape.
Secure access from anywhere
Secure Access from Anywhere: The Advantages of iBoss Cloud
In today’s interconnected world, the ability to access company resources securely from anywhere has become a necessity for businesses. This is where iBoss Cloud shines, offering a key advantage with its secure access capabilities. With iBoss Cloud, users can enjoy secure access from any device, anytime, and anywhere.
The traditional approach to network security often relied on employees being physically present in the office to access company resources securely. However, this approach is no longer practical or efficient in today’s mobile and remote work environments. Employees need the flexibility to work from various locations and devices without compromising network security.
iBoss Cloud addresses this challenge by providing a cloud-based secure web gateway solution that allows users to connect securely to corporate networks from any device with internet access. Whether employees are working from home, on the road, or at a client’s site, they can easily and securely access company resources.
This capability offers several advantages for businesses:
- Increased Productivity: With iBoss Cloud’s secure access feature, employees can work remotely without any limitations. They have the freedom to collaborate and complete tasks regardless of their location or the device they are using. This flexibility boosts productivity and ensures work continuity even in unexpected situations.
- Enhanced Mobility: iBoss Cloud enables employees to use their preferred devices such as laptops, tablets, or smartphones while maintaining strong security measures. This mobility empowers employees to be productive on the go without compromising data protection.
- Cost Savings: By allowing secure access from anywhere, iBoss Cloud reduces the need for expensive hardware investments associated with traditional on-premises solutions. Moreover, it eliminates costs related to maintaining separate VPN solutions for remote connectivity.
- Streamlined IT Management: Centralized management through iBoss Cloud simplifies IT administration tasks related to user authentication and policy enforcement across different devices and locations. IT teams can efficiently monitor and manage user activity, ensuring a consistent security posture throughout the organization.
- Heightened Security: iBoss Cloud ensures that all remote connections are protected by robust security measures, including encryption and advanced threat detection. This safeguards sensitive company data and prevents unauthorized access, reducing the risk of data breaches.
In conclusion, iBoss Cloud’s secure access from anywhere feature empowers businesses to embrace the benefits of remote work without compromising network security. By offering flexibility, productivity gains, cost savings, streamlined IT management, and heightened security, iBoss Cloud enables organizations to adapt to the evolving work landscape while maintaining a strong security posture. Embracing this solution can help businesses thrive in today’s mobile and interconnected world.
Advanced threat protection
Advanced Threat Protection: Safeguarding Your Organization with iBoss Cloud
In today’s digital landscape, the threat of cyber attacks is ever-present. Malware, phishing attacks, and other cyber threats can wreak havoc on organizations, compromising sensitive data and disrupting business operations. This is where iBoss Cloud shines with its advanced threat protection capabilities.
iBoss Cloud offers a robust and proactive approach to defending against cyber threats. With its advanced threat protection features, it provides organizations with the confidence to navigate the digital world securely.
One of the key strengths of iBoss Cloud is its ability to detect and mitigate malware effectively. Through real-time threat intelligence and behavior analytics, it continuously monitors network traffic patterns to identify and block malicious software before it can infiltrate systems. This proactive approach ensures that organizations are protected from the latest malware strains, even those that have yet to be identified by traditional security solutions.
Phishing attacks pose a significant risk to organizations as they attempt to trick users into revealing sensitive information such as login credentials or financial details. iBoss Cloud’s advanced threat protection extends to combating phishing attacks as well. It employs sophisticated algorithms and machine learning techniques to analyze email content, URLs, and attachments for signs of phishing attempts. By flagging suspicious emails and blocking access to malicious websites, iBoss Cloud helps prevent employees from falling victim to these deceptive tactics.
In addition to malware and phishing protection, iBoss Cloud also defends against various other cyber threats that can compromise organizational security. Its comprehensive suite of security measures includes:
– Intrusion Prevention: Identifying and blocking unauthorized access attempts or suspicious activities within the network.
– Data Loss Prevention (DLP): Preventing accidental or intentional data leaks by monitoring and controlling the transmission of sensitive information.
– Advanced Firewall: Providing a strong line of defense against unauthorized network access while allowing legitimate traffic flow.
– Web Application Firewall (WAF): Protecting web applications from common vulnerabilities such as cross-site scripting (XSS) and SQL injection attacks.
By offering advanced threat protection against malware, phishing attacks, and other cyber threats, iBoss Cloud empowers organizations to stay ahead of the ever-evolving threat landscape. With its proactive approach and continuous monitoring capabilities, it provides a solid foundation for a robust cybersecurity strategy.
In conclusion, iBoss Cloud’s advanced threat protection is an invaluable asset for organizations seeking to safeguard their sensitive data and maintain a secure digital environment. By leveraging its comprehensive security measures, businesses can mitigate the risks posed by malware, phishing attacks, and other cyber threats. With iBoss Cloud as your trusted cybersecurity partner, you can focus on your core business activities with peace of mind knowing that your organization is well-protected against today’s sophisticated cyber threats.
Granular policy enforcement
Granular Policy Enforcement: Enhancing Security and Productivity with iBoss Cloud
In the digital age, businesses face the challenge of maintaining a secure and productive work environment while allowing employees to access essential applications and websites. This is where iBoss Cloud shines with its granular policy enforcement feature, offering organizations a powerful tool to control user access and block unwanted content effectively.
With iBoss Cloud’s granular policy enforcement, businesses can establish specific policies that dictate which applications and websites users can access. This level of control ensures that employees are only able to interact with approved resources, reducing the risk of data breaches, malware infections, and productivity loss.
One of the key advantages of iBoss Cloud’s granular policy enforcement is its flexibility. Administrators can define policies based on a variety of criteria such as user roles, departments, timeframes, or even individual users. This enables organizations to tailor their security measures according to their unique requirements.
By implementing granular policy enforcement, businesses can effectively block access to non-work-related websites and applications that may distract employees or pose security risks. This not only enhances productivity but also reduces the chances of falling victim to phishing attacks or inadvertently downloading malicious software.
Furthermore, iBoss Cloud’s granular policy enforcement allows for dynamic adjustments as business needs evolve. Administrators have the flexibility to update policies in real-time, granting or restricting access as necessary. For example, during critical projects or sensitive periods, certain applications or websites can be temporarily blocked or limited to specific user groups.
The ability to enforce granular policies also helps organizations achieve regulatory compliance by ensuring that sensitive data remains protected. By blocking unauthorized access to certain websites or applications that may pose compliance risks, businesses can mitigate potential legal liabilities.
In conclusion, iBoss Cloud’s granular policy enforcement feature empowers organizations with fine-grained control over user access and content filtering. By defining specific policies based on roles, departments, or individuals, businesses can enhance security, productivity, and regulatory compliance. With the flexibility to adapt policies in real-time, iBoss Cloud provides a powerful solution for businesses seeking to strike the right balance between enabling access to essential resources and mitigating potential risks associated with unapproved content.
Comprehensive visibility & reporting
Comprehensive Visibility & Reporting: Ensuring Compliance with iBoss Cloud
In the fast-paced digital landscape, organizations face the challenge of maintaining compliance with corporate policies and regulations while keeping up with evolving cybersecurity threats. This is where iBoss Cloud shines with its comprehensive visibility and reporting capabilities.
iBoss Cloud offers organizations a powerful tool to gain deep insights into user activity across their networks. With its advanced reporting features, businesses can monitor and analyze user behavior, ensuring compliance with corporate policies and industry regulations. Here’s why comprehensive visibility and reporting are crucial:
Identifying Policy Violations:
With iBoss Cloud’s detailed reporting capabilities, organizations can easily identify policy violations in real-time. By monitoring user activity, IT administrators can quickly spot any unauthorized access attempts or breaches of acceptable use policies. This proactive approach helps prevent potential security incidents before they escalate.
Ensuring Regulatory Compliance:
Compliance with industry regulations is a top priority for businesses operating in various sectors. iBoss Cloud enables organizations to generate comprehensive reports that demonstrate adherence to regulatory requirements. These reports provide evidence of compliance during audits or regulatory inspections, giving businesses peace of mind.
Monitoring Productivity:
Understanding how employees utilize their time online is essential for maintaining productivity within an organization. iBoss Cloud’s visibility and reporting features allow businesses to track internet usage patterns, identify excessive non-work-related activities, and take necessary actions to optimize productivity levels.
Detecting Insider Threats:
Insider threats pose a significant risk to organizational security. By monitoring user activity through iBoss Cloud’s comprehensive visibility features, businesses can detect any suspicious behavior or unauthorized access attempts from within their networks. Timely detection of insider threats helps mitigate potential damage and safeguard sensitive data.
Customized Reporting:
iBoss Cloud provides customizable reporting options that allow organizations to tailor reports according to their specific needs. Businesses can generate reports based on various parameters, including user activity, website categories, applications usage, and bandwidth consumption. This flexibility enables organizations to extract valuable insights for informed decision-making.
In conclusion, iBoss Cloud’s comprehensive visibility and reporting capabilities empower organizations to maintain compliance with corporate policies and regulations effectively. By monitoring user activity and generating detailed reports, businesses can identify policy violations, ensure regulatory compliance, monitor productivity levels, detect insider threats, and make informed decisions based on actionable insights. Embracing iBoss Cloud as a secure web gateway solution not only strengthens cybersecurity defenses but also helps organizations stay ahead in today’s dynamic digital landscape.
Real-time monitoring & alerting
Real-time Monitoring & Alerting: Enhancing Security with iBoss Cloud
In the ever-evolving landscape of cybersecurity, organizations need to stay vigilant and respond swiftly to potential threats. This is where iBoss Cloud’s real-time monitoring and alerting capabilities shine, providing businesses with a powerful tool to identify suspicious user activity and mitigate risks promptly.
iBoss Cloud offers real-time monitoring, allowing organizations to keep a close eye on their network traffic and user behavior. By continuously analyzing data streams, it can detect anomalies, unusual patterns, or potentially malicious activities that may go unnoticed by traditional security measures.
The ability to monitor user activity in real-time is crucial for early threat detection. Suspicious activities such as multiple failed login attempts, unauthorized access attempts, or unusually high data transfers can trigger immediate alerts. These alerts enable IT teams to investigate potential security breaches promptly and take appropriate action before any significant damage occurs.
With iBoss Cloud’s alerting system in place, organizations gain a proactive approach to cybersecurity. The system can be configured to send alerts via email or through the centralized management console, ensuring that IT teams are immediately notified of any potential threats. This allows for swift response times and the implementation of necessary security measures to neutralize risks effectively.
Real-time monitoring and alerting also contribute significantly to incident response management. When an alert is triggered, IT teams can quickly assess the situation by accessing detailed logs and reports provided by iBoss Cloud. This information helps them understand the nature of the threat and take appropriate steps to mitigate it promptly.
Furthermore, iBoss Cloud’s real-time monitoring and alerting features provide valuable insights into user behavior trends. By analyzing patterns over time, organizations can identify potential vulnerabilities or areas where additional security measures may be required. This proactive approach strengthens overall network security posture and helps prevent future incidents.
In conclusion, iBoss Cloud’s real-time monitoring and alerting capabilities offer a proactive defense against cyber threats by quickly identifying suspicious user activity. With immediate alerts and detailed reports, organizations can respond swiftly, mitigate risks, and enhance their overall security posture. By leveraging this powerful feature, businesses can stay one step ahead in the ongoing battle against cybercrime and protect their valuable data and assets effectively.
Multi-tenancy support
Unlocking Scalability and Efficiency with iBoss Cloud’s Multi-Tenancy Support
In the realm of cybersecurity, managing multiple tenants within a single platform can be a challenging task for organizations. However, iBoss Cloud rises to the occasion by offering a remarkable solution: multi-tenancy support. This feature allows businesses to effortlessly manage multiple tenants within a single instance of the platform, ensuring easy scalability without the added cost or complexity of managing separate instances for each tenant organization.
What is Multi-Tenancy?
Multi-tenancy is a software architecture concept that enables a single instance of an application or platform to serve multiple customers or tenants simultaneously. Each tenant operates independently and securely within their designated environment, ensuring data privacy and isolation.
The Power of iBoss Cloud’s Multi-Tenancy Support
iBoss Cloud’s multi-tenancy support empowers organizations to efficiently manage their tenants within one unified platform. Here are some key benefits:
Streamlined Scalability:
With iBoss Cloud’s multi-tenancy support, scaling your infrastructure becomes hassle-free. As your organization grows or demands fluctuate, you can easily add new tenants without the need for additional instances or complex configurations. This flexibility ensures that your resources are optimally utilized while avoiding unnecessary costs.
Cost-Efficiency:
Managing separate instances for each tenant can be expensive, requiring additional hardware, maintenance, and administrative efforts. By consolidating multiple tenants within one instance, iBoss Cloud eliminates these extra costs associated with maintaining separate environments. This cost-effective approach allows organizations to allocate their resources more efficiently.
Simplified Administration:
iBoss Cloud’s multi-tenancy support offers centralized administration and management capabilities. Administrators can easily configure policies, monitor network activity, and generate reports across all tenants from a single control panel. This streamlined approach saves time and effort while maintaining consistent security measures across the entire organization.
Enhanced Security:
Each tenant within iBoss Cloud’s multi-tenancy environment operates independently, ensuring data privacy and isolation. This segregation prevents unauthorized access or data leakage between tenants, providing an additional layer of security. With iBoss Cloud, organizations can confidently protect their sensitive information without compromising efficiency or scalability.
Conclusion
iBoss Cloud’s multi-tenancy support is a game-changer for organizations seeking scalable and efficient cybersecurity solutions. By consolidating multiple tenants within a single instance of the platform, businesses can effortlessly scale their infrastructure while reducing costs and administrative complexities. This feature empowers organizations to streamline their operations, enhance security measures, and allocate resources more effectively. Embrace iBoss Cloud’s multi-tenancy support today and unlock the potential for seamless scalability and simplified management within your organization.
Integration with leading identity providers
Integration with Leading Identity Providers: Simplifying Authentication with iBoss Cloud
In today’s digital landscape, managing multiple user identities across various platforms can be a cumbersome task for organizations. However, with iBoss Cloud’s integration with leading identity providers such as Okta, Microsoft Azure AD, and Google G Suite, this challenge becomes a thing of the past.
One of the standout features of iBoss Cloud is its ability to seamlessly integrate with these popular identity providers. This integration allows organizations to leverage their existing user identities for secure authentication into the iBoss Cloud platform. Instead of creating new user accounts from scratch, employees can simply use their existing credentials to access the platform.
The benefits of this integration are significant. First and foremost, it simplifies the authentication process for users. They no longer need to remember additional usernames and passwords specific to iBoss Cloud. By leveraging their existing identities, they can seamlessly access the platform without any extra hassle.
Furthermore, integrating with leading identity providers enhances security. These providers have robust security measures in place to protect user credentials and prevent unauthorized access. Leveraging their authentication mechanisms adds an extra layer of protection to the iBoss Cloud platform.
From an administrative perspective, integrating with leading identity providers streamlines user management processes. Organizations can centralize user provisioning and deprovisioning through their chosen identity provider. This means that when an employee joins or leaves the organization, their access to iBoss Cloud can be easily managed through one centralized system.
Additionally, this integration enables organizations to enforce consistent security policies across all platforms that are connected to the chosen identity provider. This ensures that security measures applied within Okta, Microsoft Azure AD, or Google G Suite extend seamlessly into the iBoss Cloud environment.
In conclusion, iBoss Cloud’s integration with leading identity providers offers numerous advantages for organizations seeking a secure and streamlined authentication experience. By leveraging existing identities from Okta, Microsoft Azure AD, or Google G Suite, employees can access the iBoss Cloud platform effortlessly. This integration not only simplifies the authentication process but also enhances security and centralizes user management. With iBoss Cloud, organizations can enjoy a seamless and secure authentication experience while leveraging their existing identity infrastructure.
24/7 customer support
24/7 Customer Support: A Key Advantage of iBoss Cloud
In the realm of technology solutions, having reliable and accessible customer support is crucial. That’s why iBoss Cloud stands out with its exceptional 24/7 customer support. With this advantage, iBoss Cloud ensures that customers have the assistance they need whenever they need it most.
Technology issues can arise at any time, and businesses cannot afford to wait for support during critical moments. With iBoss Cloud’s round-the-clock customer support, organizations can rest assured that help is just a call or message away, regardless of the time zone or location.
The benefits of 24/7 customer support are numerous. Firstly, it provides peace of mind to businesses using iBoss Cloud, knowing that expert assistance is available at any hour. Whether it’s a minor query or a critical issue impacting operations, customers can rely on the dedicated support team to provide prompt and effective solutions.
iBoss Cloud’s customer support team consists of knowledgeable professionals who understand the intricacies of the platform. They possess extensive expertise in addressing technical challenges and guiding customers through various features and functionalities. Their goal is to ensure that customers make the most out of their iBoss Cloud experience.
Furthermore, 24/7 customer support enables businesses to maintain uninterrupted operations. In case of unexpected disruptions or emergencies, having immediate access to technical assistance helps minimize downtime and mitigate potential losses. This level of support ensures that organizations can swiftly overcome any obstacles they encounter while utilizing iBoss Cloud.
The convenience and reliability offered by iBoss Cloud’s 24/7 customer support contribute significantly to overall customer satisfaction. Organizations feel valued when their concerns are promptly addressed, fostering long-term relationships built on trust and reliability.
In conclusion, one of the standout advantages of iBoss Cloud is its commitment to providing 24/7 customer support. This feature ensures that businesses using the platform have access to expert assistance whenever they need it most. With a dedicated support team available at all times, organizations can maximize the benefits of iBoss Cloud while minimizing disruptions and maintaining smooth operations.
High Cost
High Cost: A Consideration for iBoss Cloud
While iBoss Cloud offers a comprehensive suite of features and benefits, it is important to acknowledge that one potential drawback of this solution is its relatively high cost compared to other cloud-based alternatives. This can pose challenges for businesses, particularly smaller ones with limited budgets.
The advanced technology and robust security measures implemented by iBoss Cloud contribute to its higher price point. The investment required may be a barrier for some organizations, especially those operating on tight financial constraints or in industries where cost optimization is a top priority.
However, it is essential to consider the value that iBoss Cloud brings to the table. Its advanced web filtering, data loss prevention, malware defense, and network protection capabilities provide organizations with a powerful toolset to mitigate cybersecurity risks effectively. The scalability and flexibility offered by the cloud-based architecture also allow businesses to adapt and grow without significant infrastructure investments.
When evaluating the cost of iBoss Cloud, it is crucial to consider the potential consequences of not having robust cybersecurity measures in place. The financial impact of a data breach or cyber attack can be far more significant than the initial investment required for implementing a secure web gateway solution like iBoss Cloud.
Organizations considering iBoss Cloud should carefully assess their specific needs and budgetary constraints. It may be beneficial to explore alternative options and compare pricing structures with other cloud-based solutions available in the market. Additionally, reaching out to iBoss representatives or engaging with industry experts can help gain insights into potential cost-saving strategies or customized pricing plans that align better with specific business requirements.
Ultimately, while the higher cost may be a limiting factor for some businesses, it is essential to weigh this against the comprehensive security features and advantages offered by iBoss Cloud. Making an informed decision based on an organization’s unique circumstances will ensure that they choose a solution that strikes the right balance between cost-effectiveness and cybersecurity efficacy.
Limited Features
Limited Features: A Drawback of iBoss Cloud
While iBoss Cloud is undoubtedly a powerful secure web gateway solution, it does have one notable drawback: limited features. Compared to other cloud-based solutions available in the market, iBoss Cloud may fall short in terms of its feature set, potentially hindering businesses from fully maximizing their investment.
One of the key factors that organizations consider when choosing a cloud-based security platform is the range of features it offers. Businesses want a solution that can address their diverse needs and provide comprehensive protection against evolving cyber threats. However, some users may find that iBoss Cloud’s feature set is not as extensive as they would prefer.
The limited features of iBoss Cloud can be problematic for businesses seeking specific functionalities or advanced capabilities. It may not offer certain niche features or highly specialized tools that are available in other solutions. This can be particularly challenging for organizations operating in industries with unique regulatory requirements or complex network infrastructures.
Moreover, businesses looking for integration with third-party applications or seamless compatibility with existing systems may find themselves restricted by the limited feature set of iBoss Cloud. Lack of integration options can hinder workflow efficiency and limit the ability to leverage existing investments in complementary technologies.
However, it’s important to note that while iBoss Cloud may have limitations compared to some competitors, it still provides essential security features such as web filtering, data loss prevention, and malware defense. These core functionalities remain robust and effective in safeguarding networks and data against a wide range of cyber threats.
Ultimately, when evaluating iBoss Cloud as a potential solution, businesses should carefully assess their specific requirements and determine if the available features align with their needs. It’s advisable to conduct thorough research and consider alternative options to ensure that all critical functionalities are adequately addressed before making an investment decision.
In conclusion, while limited features may be considered a con of iBoss Cloud compared to some other cloud-based solutions on the market, it’s crucial to weigh this drawback against the platform’s overall benefits, such as its cloud-based architecture, scalability, and threat intelligence capabilities. By conducting a comprehensive evaluation, businesses can make an informed decision that best aligns with their unique security requirements and operational goals.
Poor Support
Poor Support: A Concern for iBoss Cloud Customers
When it comes to choosing a secure web gateway solution, reliable customer support is crucial. Unfortunately, one con that has been reported by some iBoss Cloud customers is the poor quality of support provided by the company. This issue can leave customers feeling frustrated and unsupported when they encounter problems or need assistance.
One of the main concerns raised by users is the unreliability of iBoss Cloud’s customer support. Some customers have reported difficulties in reaching a knowledgeable support representative promptly. Lengthy response times and delays in issue resolution have been cited as common frustrations. This can be particularly problematic when businesses are facing urgent security concerns or network disruptions that require immediate attention.
Furthermore, there have been complaints about the lack of effective communication between customers and iBoss Cloud’s support team. Clear and timely communication is vital in troubleshooting issues and ensuring that customers understand the steps being taken to resolve their problems. Instances of miscommunication or inadequate explanations have left some users feeling dissatisfied and unsure about the progress being made.
The impact of poor support extends beyond just technical issues. It can hinder organizations’ ability to maximize their investment in iBoss Cloud, as they may struggle to fully utilize its features or address specific configuration requirements without adequate guidance from support staff.
While it’s important to note that experiences with customer support can vary among different users, it is essential for iBoss Cloud to address these concerns promptly. Improving the quality and responsiveness of their customer support will not only enhance user satisfaction but also strengthen their reputation as a reliable provider in the secure web gateway market.
In conclusion, poor customer support has been identified as a downside for some users of iBoss Cloud. Addressing this issue should be a priority for iBoss Cloud to ensure that their customers receive timely and effective assistance whenever they need it. By investing in improving their support infrastructure, iBoss Cloud can enhance user experience and build stronger relationships with their customer base.
Security Concerns
Security Concerns: A Closer Look at iBoss Cloud
iBoss Cloud, a renowned secure web gateway solution, has gained popularity for its comprehensive security features and ability to protect organizations from cyber threats. However, like any technology, it is not without its drawbacks. One notable concern that has been raised regarding iBoss Cloud is the potential security flaws that could leave customer data vulnerable to malicious actors.
Despite offering multiple layers of security, reports have surfaced regarding possible vulnerabilities within the iBoss Cloud system. These vulnerabilities could potentially be exploited by cybercriminals to gain unauthorized access to sensitive data or compromise network integrity.
While iBoss Cloud utilizes advanced threat intelligence and behavior analytics to detect and prevent malware attacks, no system is entirely immune to new or evolving threats. The ever-changing landscape of cybersecurity requires constant vigilance and regular updates to stay ahead of potential vulnerabilities.
It is important for organizations considering implementing iBoss Cloud to be aware of these reported security concerns and take appropriate measures to mitigate any risks. This may include regularly updating the system with the latest patches and firmware releases provided by iBoss Networks, as well as implementing additional security measures such as strong access controls and encryption protocols.
Furthermore, organizations should ensure they have proper incident response plans in place in case a security breach occurs. Prompt detection and response are crucial in minimizing the potential impact of any security incidents.
It’s worth noting that while there have been reports of security flaws in iBoss Cloud, it is essential to consider the overall track record of the product. Every technology solution faces occasional vulnerabilities, but it is how these issues are addressed and resolved that truly matters.
iBoss Networks has demonstrated a commitment to addressing reported vulnerabilities promptly through regular updates and patches. They work closely with their customers to ensure their systems remain secure and resilient against emerging threats.
In conclusion, while there have been reports of security flaws within iBoss Cloud, it remains an effective secure web gateway solution when implemented and managed properly. By staying informed about potential vulnerabilities, regularly updating the system, and implementing additional security measures, organizations can maximize the benefits of iBoss Cloud while minimizing the associated risks. As with any technology solution, a proactive approach to security is key in maintaining a robust and resilient infrastructure.