Unveiling the Power of Network Infrastructure: Building the Foundation for Seamless Connectivity
Unveiling the Power of Network Infrastructure: Building the Foundation for Seamless Connectivity
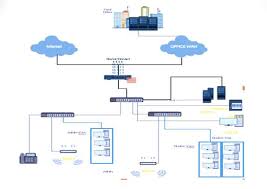
Network Infrastructure: The Backbone of Modern Connectivity
In today’s digital age, network infrastructure plays a vital role in keeping individuals and businesses connected. From the internet we use at home to the vast networks that power global enterprises, network infrastructure forms the backbone of modern connectivity. In this article, we will explore what network infrastructure is, its components, and its significance in our interconnected world.
Network infrastructure refers to the hardware, software, and protocols that enable the transmission of data between devices within a network. It encompasses a wide range of technologies such as routers, switches, servers, cables, and wireless access points. These components work together to facilitate the seamless flow of information across local area networks (LANs), wide area networks (WANs), and the internet.
At its core, network infrastructure serves as a platform for communication and data exchange. It allows computers, smartphones, tablets, and other devices to connect with each other locally or across vast distances. Without robust network infrastructure in place, many of the services we rely on today would not be possible.
One crucial aspect of network infrastructure is its ability to provide reliable and secure connectivity. Whether it’s sending an email or conducting a video conference with colleagues halfway around the world, we expect our connections to be stable and secure. Network infrastructure ensures that data packets are delivered efficiently and securely from one point to another.
In addition to connectivity, network infrastructure also enables resource sharing. Through shared servers or cloud-based solutions, businesses can centralize their data storage and applications while allowing employees to access them from anywhere with an internet connection. This level of flexibility enhances productivity and collaboration within organizations.
Scalability is another key feature of network infrastructure. As businesses grow or experience fluctuations in demand, their networks must be able to adapt accordingly. Scalable network infrastructure allows for easy expansion without compromising performance or security.
Moreover, network infrastructure plays a significant role in ensuring data security. With cyber threats becoming more sophisticated, network infrastructure must incorporate robust security measures to protect sensitive information. Firewalls, encryption protocols, and intrusion detection systems are just a few examples of the security measures implemented within network infrastructure.
In recent years, the rise of emerging technologies such as cloud computing, the Internet of Things (IoT), and artificial intelligence (AI) has placed even greater importance on network infrastructure. These technologies generate vast amounts of data that require efficient transmission and processing. Without a reliable and robust network infrastructure, the potential of these technologies would be severely limited.
In conclusion, network infrastructure is the foundation upon which our interconnected world operates. It enables communication, resource sharing, scalability, and data security. As technology continues to advance and our reliance on connectivity grows, investing in robust and future-proof network infrastructure becomes increasingly crucial for individuals and businesses alike. By doing so, we can ensure that our networks remain reliable, secure, and capable of supporting the innovations of tomorrow.
7 Essential Tips for Secure and Efficient Network Infrastructure in the UK
- Ensure you have a secure firewall in place to protect your network from malicious attacks.
- Regularly monitor and update your network infrastructure to ensure optimal performance and security.
- Utilise virtual private networks (VPNs) for remote access to sensitive data or systems.
- Implement robust authentication protocols such as two-factor authentication or biometric identification for added security measures when accessing the network infrastructure remotely.
- Utilise encryption technologies such as TLS/SSL to protect data in transit between devices on the network infrastructure, as well as data stored on the network itself.
- Make use of cloud services where possible in order to reduce costs and increase scalability of the network infrastructure without compromising on security measures or performance levels
- Monitor user activity within the network environment for suspicious behaviour that could indicate a potential security breach or malicious attack
Ensure you have a secure firewall in place to protect your network from malicious attacks.
Protecting Your Network: The Importance of a Secure Firewall
In today’s digital landscape, network security is of paramount importance. With the ever-increasing number of cyber threats, it is crucial to safeguard your network from malicious attacks. One essential element in fortifying your network infrastructure is ensuring that you have a secure firewall in place.
A firewall acts as a protective barrier between your internal network and the outside world. It monitors and filters incoming and outgoing network traffic based on predetermined security rules. By analyzing data packets, a firewall can identify potential threats and block unauthorized access attempts.
The significance of having a secure firewall cannot be overstated. Here are some key reasons why it should be an integral part of your network infrastructure:
- Protection against External Threats: A firewall acts as the first line of defense against external threats, such as hackers, malware, and viruses. It examines incoming traffic and blocks any suspicious or malicious activity, preventing unauthorized access to your network.
- Network Segmentation: Firewalls allow you to segment your network into different zones or subnets based on security requirements. This segregation helps contain potential breaches by limiting the impact an attacker can have on your entire network if they manage to infiltrate one area.
- Application Control: Firewalls offer granular control over applications that can access your network. By setting up specific rules, you can restrict or allow certain applications based on their legitimacy and relevance to your business operations.
- VPN Connectivity: Virtual Private Networks (VPNs) create encrypted connections between remote users and your internal network. A firewall can provide secure VPN connectivity, allowing employees to access company resources while working remotely without compromising data security.
- Traffic Monitoring and Reporting: Firewalls provide valuable insights into network traffic patterns through logs and reports. This information helps administrators identify potential vulnerabilities or suspicious activities, enabling them to take proactive measures to enhance security.
To ensure an effective firewall implementation, consider the following best practices:
– Regularly update your firewall software to protect against emerging threats and vulnerabilities.
– Define and enforce strong security policies that align with your organization’s needs and industry standards.
– Conduct regular security audits to identify any weaknesses or misconfigurations in your firewall settings.
– Implement multi-factor authentication for remote access to further enhance security.
Remember, a secure firewall is not a one-time solution. It requires ongoing monitoring, maintenance, and updates to stay ahead of evolving threats. By prioritizing the installation and proper configuration of a secure firewall, you can significantly reduce the risk of cyberattacks and protect your network infrastructure from potential harm.
Regularly monitor and update your network infrastructure to ensure optimal performance and security.
Regularly Monitor and Update: The Key to Optimal Network Infrastructure Performance and Security
In the fast-paced world of technology, network infrastructure is constantly evolving. To ensure optimal performance and security, it is crucial to regularly monitor and update your network infrastructure. This simple yet essential tip can save you from potential issues and keep your network running smoothly.
Monitoring your network infrastructure involves keeping a close eye on its performance, identifying any bottlenecks or vulnerabilities, and taking proactive measures to address them. By monitoring key metrics such as bandwidth usage, latency, and device health, you can detect any anomalies or signs of strain on your network.
Regular updates are equally important. Technology is constantly evolving, and so are the threats that target network infrastructures. Software updates often include bug fixes, security patches, and performance improvements that help safeguard against potential vulnerabilities. By keeping your network infrastructure up to date with the latest firmware releases, software updates, and security protocols, you can stay one step ahead of potential threats.
Optimal performance goes hand in hand with security. Outdated or unpatched software can leave your network vulnerable to cyber attacks. By regularly updating your network infrastructure’s software components, you ensure that any known security vulnerabilities are patched promptly. This reduces the risk of unauthorized access or data breaches.
Moreover, regular monitoring allows you to identify areas where your network may be underperforming or experiencing congestion. By addressing these issues promptly through traffic optimization techniques or hardware upgrades, you can maintain a high-quality user experience for all connected devices.
Another benefit of regular monitoring is the ability to anticipate future needs. By analyzing usage patterns and trends over time, you can identify areas where additional resources may be required before they become critical bottlenecks. This proactive approach helps prevent unexpected downtime or service disruptions.
It’s worth noting that monitoring and updating your network infrastructure doesn’t have to be a daunting task. Many tools and solutions are available that simplify the process, providing real-time insights into network performance and automating software updates. By leveraging these tools, you can streamline the monitoring and updating process, saving time and effort while ensuring the best possible network performance and security.
In conclusion, regularly monitoring and updating your network infrastructure is essential for maintaining optimal performance and security. By staying vigilant, you can identify potential issues before they escalate, patch vulnerabilities promptly, and ensure that your network is ready to handle the demands of today’s digital landscape. So make it a habit to monitor your network’s health regularly and keep your infrastructure up to date – it’s a small investment that yields significant benefits in the long run.
Utilise virtual private networks (VPNs) for remote access to sensitive data or systems.
Enhancing Security: Utilizing Virtual Private Networks (VPNs) for Remote Access to Sensitive Data or Systems
In an era where remote work is becoming increasingly prevalent, ensuring the security of sensitive data and systems is of paramount importance. One effective measure to safeguard this information is through the use of Virtual Private Networks (VPNs). In this article, we will explore how VPNs can enhance security when accessing sensitive data or systems remotely.
A VPN creates a secure and encrypted connection between a user’s device and a private network. It acts as a protective tunnel, shielding data from potential threats such as hackers or unauthorized access. By utilizing VPNs, individuals can establish a secure connection to their organization’s network, even when working remotely.
When accessing sensitive data or systems remotely, the use of VPNs adds an extra layer of protection. It ensures that confidential information remains encrypted and inaccessible to prying eyes. This is especially crucial when connecting via unsecured public Wi-Fi networks, which are notorious for their vulnerability to cyber attacks.
By routing internet traffic through the VPN server, individuals can mask their IP address and location. This feature enhances anonymity and prevents potential attackers from tracking online activities. Consequently, utilizing VPNs not only safeguards sensitive data but also protects individual privacy.
Furthermore, VPNs enable organizations to enforce access controls more effectively. They allow administrators to define who can access specific resources within the network and under what conditions. By implementing strict authentication protocols, organizations can ensure that only authorized personnel with valid credentials gain entry to sensitive systems or data.
From a compliance standpoint, utilizing VPNs for remote access can help organizations meet regulatory requirements regarding data protection and privacy. Many industries have strict guidelines in place to safeguard customer information or intellectual property. Employing VPNs demonstrates a commitment to maintaining robust security measures and adhering to industry standards.
When selecting a VPN service provider, it is essential to choose one with a strong reputation for security and reliability. Look for providers that offer end-to-end encryption, multi-factor authentication, and regular security updates. Additionally, consider the provider’s track record in terms of data breaches or vulnerabilities.
In conclusion, utilizing Virtual Private Networks (VPNs) for remote access to sensitive data or systems is a valuable security measure. VPNs encrypt data, protect privacy, and enable organizations to enforce access controls effectively. By implementing VPNs, individuals and organizations can significantly reduce the risk of unauthorized access or data breaches when working remotely. Prioritizing security in remote access practices ensures that sensitive information remains protected, regardless of the user’s location or network used.
Implement robust authentication protocols such as two-factor authentication or biometric identification for added security measures when accessing the network infrastructure remotely.
Enhancing Network Infrastructure Security with Robust Authentication Protocols
In an era where remote work and connectivity are increasingly prevalent, securing network infrastructure has become a top priority for businesses. One effective measure to bolster security is the implementation of robust authentication protocols, such as two-factor authentication (2FA) or biometric identification. These additional layers of verification provide an extra level of protection when accessing network infrastructure remotely.
Two-factor authentication is a widely used method that requires users to provide two separate pieces of evidence to verify their identity. Typically, this involves something the user knows (such as a password or PIN) and something they possess (such as a unique code sent to their mobile device). By combining these two factors, even if one factor is compromised, the attacker would still need access to the second factor to gain entry.
Biometric identification takes authentication a step further by using unique physical or behavioral characteristics for verification. This can include fingerprints, facial recognition, iris scans, or voice recognition. Biometrics offer a highly secure and convenient way to authenticate users as these characteristics are difficult to replicate or forge.
Implementing these robust authentication protocols provides several benefits for network infrastructure security. Firstly, it significantly reduces the risk of unauthorized access by adding an extra layer of verification beyond just passwords. Even if someone manages to obtain login credentials, they would still need access to the second factor or possess the specific biometric traits required for entry.
Secondly, these protocols enhance user accountability and traceability. With 2FA or biometric identification in place, it becomes easier to track and identify individuals who attempt unauthorized access or malicious activities within the network infrastructure. This strengthens overall security posture and aids in incident response efforts.
Moreover, implementing robust authentication protocols helps protect against common cyber threats such as phishing attacks and brute-force password cracking attempts. Even if an attacker manages to trick a user into revealing their password through deceptive means, they would still be unable to gain access without the additional authentication factor or biometric data.
It is important to note that while robust authentication protocols provide added security, they should be implemented alongside other essential security measures. This includes regular software updates, strong password policies, network monitoring, and employee education on best practices for cybersecurity.
In conclusion, implementing robust authentication protocols like two-factor authentication or biometric identification is a proactive step towards enhancing the security of network infrastructure. These additional layers of verification significantly reduce the risk of unauthorized access and provide better accountability. By incorporating these measures alongside other security practices, businesses can better protect their network infrastructure from evolving cyber threats and ensure secure remote access for their employees.
Utilise encryption technologies such as TLS/SSL to protect data in transit between devices on the network infrastructure, as well as data stored on the network itself.
Protecting Data in Transit and at Rest: The Power of Encryption Technologies
In today’s interconnected world, where data flows seamlessly between devices and networks, ensuring the security and privacy of sensitive information is of paramount importance. One crucial tip for safeguarding your network infrastructure is to utilize encryption technologies such as TLS/SSL. By implementing these protocols, you can protect data in transit between devices on the network infrastructure, as well as data stored on the network itself.
Transport Layer Security (TLS) and Secure Sockets Layer (SSL) are cryptographic protocols that establish secure connections between devices over a network. They provide an encrypted tunnel through which data can travel securely, shielding it from potential eavesdropping or unauthorized access.
When data is transmitted from one device to another within a network, it often travels across multiple intermediate points before reaching its destination. During this journey, it is vulnerable to interception by malicious actors who may attempt to capture sensitive information for nefarious purposes. By implementing TLS/SSL encryption, you can significantly reduce the risk of data interception and maintain its confidentiality.
Encryption works by scrambling the data using complex algorithms so that only authorized recipients with the appropriate decryption keys can understand it. This ensures that even if intercepted, the intercepted data remains unreadable and useless to unauthorized individuals.
Additionally, encryption technologies play a vital role in securing data stored on the network infrastructure itself. Networks often contain servers or storage devices that hold vast amounts of sensitive information. Encrypting this stored data adds an extra layer of protection against unauthorized access or breaches.
Implementing TLS/SSL encryption requires careful configuration and management. It involves obtaining digital certificates from trusted certificate authorities to validate the authenticity of websites or services using these protocols. Regular updates and patches should also be applied to ensure any vulnerabilities are addressed promptly.
By utilizing encryption technologies such as TLS/SSL within your network infrastructure, you demonstrate a commitment to protecting sensitive information both during transmission and while at rest. This not only helps safeguard your organization’s data but also enhances trust among your customers and partners.
Remember, encryption is just one piece of the security puzzle. It should be complemented by other best practices such as strong access controls, regular security audits, and employee awareness training. By adopting a holistic approach to network security, you can fortify your infrastructure against potential threats and ensure the integrity and confidentiality of your valuable data.
In conclusion, encryption technologies like TLS/SSL are powerful tools for protecting data in transit between devices on the network infrastructure and data stored on the network itself. By implementing these protocols, you can significantly enhance the security of your network, reduce the risk of data breaches, and instill confidence in those who entrust you with their sensitive information.
Make use of cloud services where possible in order to reduce costs and increase scalability of the network infrastructure without compromising on security measures or performance levels
Unlocking Cost Efficiency and Scalability with Cloud Services in Network Infrastructure
In the ever-evolving landscape of network infrastructure, businesses are constantly seeking ways to optimize their operations while keeping costs in check. One powerful solution that has emerged is leveraging cloud services. By harnessing the capabilities of the cloud, businesses can reduce costs and increase scalability without compromising on security or performance levels.
Traditionally, building and maintaining an on-premises network infrastructure involved significant upfront investments in hardware, software licenses, and ongoing maintenance costs. However, with cloud services, businesses can shift from a capital expenditure (CapEx) model to an operational expenditure (OpEx) model. This means that instead of purchasing and managing physical infrastructure, they can access computing resources on-demand through a pay-as-you-go subscription model.
The cost savings achieved by adopting cloud services for network infrastructure are significant. Businesses no longer need to invest in expensive hardware or worry about equipment becoming outdated. Instead, they can rely on the cloud provider’s infrastructure, which is regularly updated and maintained to meet industry standards. This eliminates the need for costly hardware upgrades and reduces ongoing maintenance expenses.
Furthermore, cloud services offer unparalleled scalability. With traditional on-premises infrastructure, scaling up or down often required substantial investments in additional hardware or software licenses. However, cloud providers offer flexible options where businesses can easily adjust their computing resources based on their needs. Whether it’s increasing capacity during peak periods or scaling down during slower times, the cloud allows for seamless scalability without disruption.
Moreover, security is a top concern when it comes to network infrastructure. Thankfully, reputable cloud service providers prioritize security measures to protect customer data. They employ robust encryption protocols, implement multi-factor authentication mechanisms, and maintain stringent access controls to safeguard sensitive information. By leveraging these secure cloud services, businesses can ensure that their network infrastructure remains protected against cyber threats while benefiting from cost savings and scalability.
Performance is another critical aspect of network infrastructure. The cloud offers high-speed, reliable connections that can handle vast amounts of data traffic. With a well-designed cloud architecture, businesses can achieve low latency and quick response times, ensuring optimal performance for their applications and services.
In summary, embracing cloud services for network infrastructure presents a compelling opportunity to reduce costs, increase scalability, and maintain high levels of security and performance. By leveraging the expertise and infrastructure of reputable cloud service providers, businesses can focus on their core operations while leaving the management of network infrastructure to the experts. This shift from a capital-intensive model to an operational expenditure model empowers businesses to allocate resources more efficiently and adapt to changing demands with ease. As technology continues to advance, harnessing the power of the cloud will undoubtedly play a pivotal role in shaping the future of network infrastructure.
Monitor user activity within the network environment for suspicious behaviour that could indicate a potential security breach or malicious attack
Monitoring User Activity: Safeguarding Network Infrastructure
In the digital landscape, where threats to network security are ever-present, it is crucial for businesses to adopt proactive measures to protect their network infrastructure. One effective tip that can significantly enhance security is monitoring user activity within the network environment for suspicious behavior. By closely observing user actions, businesses can swiftly identify potential security breaches or malicious attacks and take immediate action to mitigate any potential damage.
User activity monitoring involves tracking and analyzing the actions performed by individuals within the network. This includes monitoring logins, file access, system changes, and other activities that occur on the network. By implementing robust monitoring tools and technologies, businesses gain valuable insights into user behavior patterns, allowing them to detect any anomalies that may indicate a security threat.
Detecting suspicious behavior is essential because it enables organizations to respond promptly. Unusual activities such as repeated failed login attempts, unauthorized access attempts to sensitive data or systems, or abnormal data transfers can serve as warning signs of a potential breach. By actively monitoring these activities, businesses can quickly identify and investigate any suspicious behavior before it escalates into a full-blown security incident.
Implementing user activity monitoring not only helps in identifying external threats but also addresses internal risks. Insider threats pose a significant risk to network security as employees with privileged access may misuse their privileges or inadvertently compromise sensitive information. Monitoring user activity allows businesses to identify any unusual or unauthorized actions performed by employees and take appropriate measures to mitigate the risk.
Moreover, user activity monitoring serves as a deterrent against potential malicious actors. The knowledge that their actions are being monitored acts as a deterrent for individuals seeking to exploit vulnerabilities within the network infrastructure. This proactive approach helps create a secure environment that discourages unauthorized access attempts and reduces the likelihood of successful attacks.
To effectively monitor user activity within the network environment, businesses should invest in advanced security information and event management (SIEM) systems or specialized user behavior analytics (UBA) tools. These technologies provide real-time monitoring, analysis, and alerting capabilities to identify suspicious behavior promptly. Additionally, implementing robust access controls, user authentication mechanisms, and regular security awareness training for employees further strengthens the overall security posture.
In conclusion, monitoring user activity within the network environment is a vital tip for safeguarding network infrastructure. By closely observing user actions and detecting suspicious behavior, businesses can proactively identify potential security breaches or malicious attacks. This allows them to respond swiftly and effectively, minimizing the impact of any potential threats. By investing in advanced monitoring tools and implementing robust security measures, organizations can create a secure network environment that protects sensitive data and ensures business continuity in today’s evolving threat landscape.
Latest articles
- Boosting Success: Strategies for Personal Growth and Achievement
- Discover the Top Project Management Software Solutions for Your Business
- Unlocking Team Efficiency with Atlassian Jira Software
- Unlocking Efficiency: The Asta Powerproject Advantage in Construction Project Management
- The Essential Role of an Assistant Project Manager in Project Success
Latest comments
Categories
- acronis
- ad agency
- adobe
- ads marketing
- affiliate marketing
- agency web
- agile
- agile project management
- analytics cloud
- apm
- app
- apps
- asana
- assistant
- assistant manager
- associate
- association of project management
- asta
- atlassian
- business advisory
- business consultant
- business consulting
- business services
- certificate courses
- certificate programs
- cloud
- cloud computing
- cloud hosting
- cloud linux
- cloud platform
- cloud server
- cloud web hosting
- company services
- computer
- computer course
- computing
- construction
- construction management
- consulting companies
- consulting firms
- consulting services
- cost management
- customizable
- data platform
- development
- digital agencies
- digital agency
- digital marketer
- digital marketers
- digital marketing
- digital marketing agencies
- digital marketing agency
- digital marketing companies
- digital marketing company
- digital marketing service
- digital marketing services
- digital strategy
- digitalmarketer
- engine
- free
- github
- google cloud
- google cloud platform
- greencloud
- iaas
- infrastructure as a service
- internet
- internet marketing
- internet marketing agency
- internet marketing company
- internet marketing firm
- internet marketing service
- internet marketing services
- internet media marketing
- internet of things
- jira
- junior
- lean
- lean projects
- leeds
- linux
- linux hosting
- london
- management
- management consultant
- management course
- management courses
- management jobs
- management skills
- management training courses
- manager
- manager jobs
- manager tools
- marketing
- marketing agency
- marketing cloud
- marketing companies
- marketing management
- marketing manager
- marketing manager software
- marketing pr
- marwick internet marketing
- media agency
- media services company
- microsoft
- monitoring tools
- mybusiness
- network security
- nottingham
- office manager
- online agency
- online backup
- online marketing
- online marketing agency
- online marketing company
- online marketing firm
- paas
- planning
- pm p
- pmbok
- pmi
- pmi certification
- pmp
- pmp certification
- pr agencies
- pr agency
- pr communications
- pr firm
- price
- prince2
- prince2 foundation
- productivity software
- program manager
- project management
- project management jobs
- project management software
- project management system
- project manager
- project planning
- project planning software
- project tracking
- project tracking software
- saas
- search engine marketing
- search marketing
- security course
- security courses
- security jobs
- sem
- seo
- service cloud
- service manager
- service marketing
- services
- services marketing
- small
- small business marketing companies
- social media
- software developer
- software engineer
- task
- task management
- task management software
- tech solutions
- technology consulting
- telecom
- thingful
- trello
- uk
- Uncategorized
- vmware
- vps
- vps server
- web application
- web hosting
- web hosting services
- web server
- webhost
- website
- website hosting
- zoho
- zoho projects